

After appearance of the newest version last July, where TDL at that time had been detected by ESET and known by Win32/Olmarik, seems still evolving.
ESET researchers specifically examined and traces TDL 4 malware consistently, and in that time period, there are phases of the appearance new variants TDL 4. Latest phase is identification of appearance new variants malware Win32/Olmasco.R TDL 4 which has been developed in some parts, especially the way rootkit infects the system, and the ability to change layout of hidden system files.
Based on analysis carried on malware components there are some changes in kernel-mode drivers, and user-mode payload, while the other components, especially the rootkit component is still the same as previous version.
These changes indicate on a two possibilities: First, there is a change order on a team who developed TDL 4. Second, TDL4 Developer commercialize or sell Bootkit Builder to other cybercrime groups.
Analysis also showed that Win32/Olmasco.R able to send information that is copied from computer victims to C & C (Command & Control server) along the installation of rootkits into victim’s computer system.
Furthermore, when there are errors on a the process, malware will send a full report about the errors that occurred to TDL4 malware developers. This report will be kind of feedback to find out the cause of failure rootkits installation.
Also found a virtual activity which contrary to the bot trackers for malware installation process, to verify if ‘dropper’ can be run on virtual environment, then information will send to C & C.
Other activities that are found is to check whether all components can be run in a virtual environment in system targeted, this activity become privilege of Win32/Olmasco.R because it have exceeded the ability of modern malware.
The composition of Boot
Components bootkit on malware has changed since the modifications in previous variant TDL4. Something different in this new variant, while MBR (Master Boot Record) is infected, then will be available space on your hard drive as a bootable backup to store malicious components, in addition, there are also differences about the way of infecting victim computer system.
First, the malware will create a bootable partition on your hard drive. If we look on partition table on your hard drive using Windows Vista or newer Windows operating systems, we will find unpartitioned (or unallocated) space on the hard drive bootable. Usually the space is large enough to accommodate components of rootkit. Sometimes even a partitioned space will be even greater. In such cases, the magnitude from malicious partition will be limited up to 50 GB. Secondly, then the malware will create a hidden partition by modifying the entry in the partition table.
Should be noted that the MBR contains a partition table at offset 0x1BE. This table consists of four parts, each entry have 6-bytes, and each are interconnected. In addition, there is maximum of four primary partitions on your hard drive and one more partition is marked active, which means from that partition OS will be booted.
Malware that overwrites will occupy an empty entry in partition table with parameters for malicious partition, mark it as active partition and turned into a VBR (Volume Boot Record) from the newly created partition, as shown in figure below:
 If an empty entry not found in partition table, then the malware will send a report on a C & C server and stop installation process. The following picture can be seen what happens to the partition table after the system successfully penetrated by TDL4 latest version.
If an empty entry not found in partition table, then the malware will send a report on a C & C server and stop installation process. The following picture can be seen what happens to the partition table after the system successfully penetrated by TDL4 latest version.
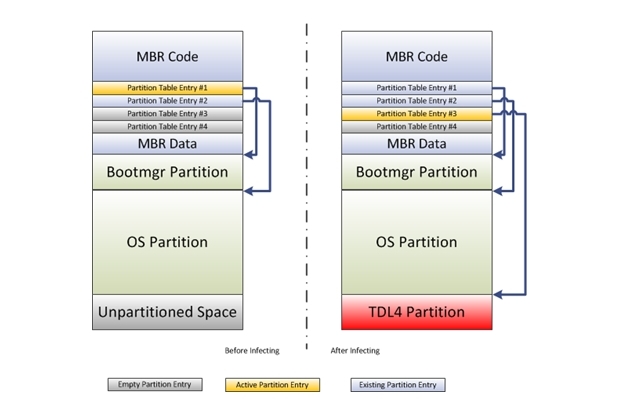 As the result from manipulation, MBR code will not be touched and the only one that needs to be changed is partition table. When a computer is infected, and control boot turned into a malicious VBR (VBR results of TDL4 partition) right after MBR code is turned off. Thus, the malware will take over control on system before operating system works.
As the result from manipulation, MBR code will not be touched and the only one that needs to be changed is partition table. When a computer is infected, and control boot turned into a malicious VBR (VBR results of TDL4 partition) right after MBR code is turned off. Thus, the malware will take over control on system before operating system works.
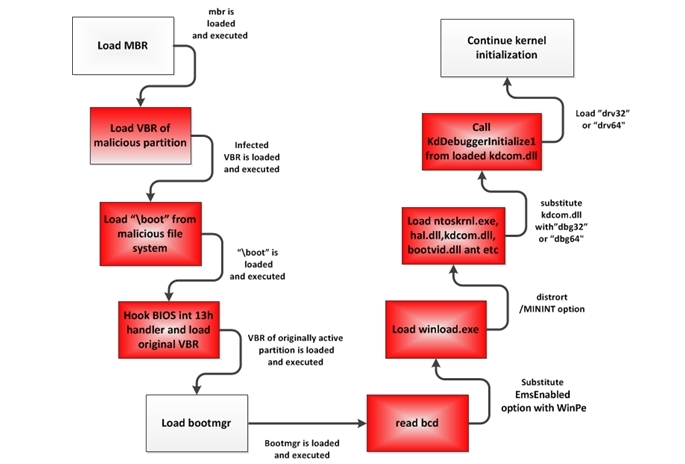
When malicious VBR accept role of such control, then he will read a file named “boot” from root directory file system TDL4, and then transfer role controls to the boot file.
Bootkit component on the latest malware variants TDL4 or identified by ESET as Win32/Olmasco.R is similar to previous version TDL4 unless name in malicious file system has been changed.
 The diagram below show image of boot process on a computer that has been infected:
The diagram below show image of boot process on a computer that has been infected:
Hidden File System
Layout from hidden file system has also changed, able to accommodate 15 files -regardless the size of available space- a new file system capacity is limited by amount of malicious partition that will enter.
“The system file which owned malware latest modification is more advanced and sophisticated than previous variants. Examples of these differences is ability malware for detecting files that corrupted which stored in hidden system files by CRC32 checksum calculation and compare with size of files stored in file header, “explained Yudhi Kukuh, Technical Consultant from PT.Prosperita-ESET.











